Why Every Researcher Needs Local Data
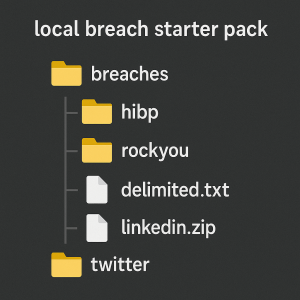
Local Breach Starter Pack is the ultimate resource for any OSINT investigator, security professional, or journalist who wants to work faster, safer, and more privately. In this guide, you’ll discover how a local breach starter pack can help you conduct more effective research and why having breach data offline is now a necessity.
🚨 Why Local Breach Data is a Game Changer: A Real-World Scenario
Imagine this: You’re running an investigation for a client whose business has been targeted by a phishing campaign. The attackers used email addresses that seem oddly familiar—but when you run the emails through public web tools, the results are slow, rate-limited, or incomplete.
You fire up your local breach archive—no throttling, no privacy concerns, no waiting. In seconds, you confirm those emails and passwords were part of several high-profile leaks—revealing how the attackers got in, which services are vulnerable, and what passwords are reused across the company.
This is the edge local breach data gives you.
Whether you’re a penetration tester, security analyst, or journalist, having offline, searchable access to breach data enables you to move faster, preserve confidentiality, and uncover connections public tools might miss.
🔥 Top 10 Breach Dumps for Your Starter Pack
Below are the must-have dumps and why each is valuable for OSINT, security research, and adversarial simulations:
- Have I Been Pwned Password Dumps
Why valuable: One of the largest and most reputable password leak collections. Enables you to verify if a password (or hash) has been compromised across hundreds of breaches. Perfect for rapid password audits and threat hunting.
Download Link — ~90 GB - RockYou & RockYou2021
Why valuable: These legendary password lists are widely used in password-cracking, pentesting, and wordlist creation. Their prevalence in the wild makes them essential for real-world attack simulations.
Download Link (RockYou2021) — 8.4 GB - Collection #1–5
Why valuable: These mega-dumps combine billions of credentials from numerous breaches. Ideal for credential stuffing, password reuse analysis, and mapping out an individual’s credential history.
Read More & Find Links — ~220 GB - Exploit.in
Why valuable: A highly useful collection for finding cleartext email-password combos, especially for targeted investigations and validating credential leaks.
Find mirrors or info on SecLists — ~24 GB - Anti-Public Combo List
Why valuable: Over 500 million credential pairs—great for bulk-checking, password audits, and uncovering account takeovers.
Find on SecLists — ~17 GB - LinkedIn Breach (2012 & 2021)
Why valuable: Two of the most impactful professional platform breaches ever. Crucial for profiling corporate users and mapping corporate data exposure.
Find via OSINT repositories or trusted infosec torrent sites — ~117M (2012), 700M (2021) - Adobe Breach
Why valuable: Useful for investigating both consumer and business email compromise. Includes encrypted passwords—often targeted in corporate phishing.
Find on SecLists or OSINT mirrors — ~4 GB - MySpace Breach
Why valuable: Large set of legacy credentials—helpful for tracking long-term password reuse and uncovering old, still-in-use email accounts.
Find on breach torrent sites — ~22 GB - Dropbox Leak
Why valuable: Focused on cloud storage users—important for assessing the risk of unauthorized file access and data exfiltration.
Find via OSINT repositories - Facebook/Twitter Leaks
Why valuable: Social media platform leaks are gold mines for social engineering, identity correlation, and mapping online footprints.
Find via OSINT sources or underground forums
🛠️ Essential Local Tools & Usage Examples
Having raw breach data is just step one. Here are must-have local tools (with examples) to make your archive actionable:
- ripgrep (
rg)
What it does: Super-fast, recursive search through huge text files—like “grep on steroids.”
rg '[email protected]' ./breaches/
Example: Instantly find all occurrences of an email in your local breach collection. - holehe
What it does: Checks if an email is registered on 100+ services, using your breach or open-source data.
holehe [email protected]
Example: Find all social media and web accounts tied to an email—locally, with privacy. - PwnedOrNot
What it does: Local checker for Have I Been Pwned leaks.
python3 pwnedornot.py -e [email protected]
Example: Check if an email appears in any of your local HIBP datasets. - Scavenger
What it does: Bulk search and analyze emails and passwords across multiple breach dumps.
python3 scavenger.py --email-list emails.txt --breach-path /data/breaches/
Example: Scan entire breach collections for multiple targets at once. - trufflehog
What it does: Finds secrets (API keys, credentials) in code and datasets.
trufflehog filesystem ./breaches/
Example: Spot potential secrets lurking in large breach dumps or codebases.
🖼️ Sample Screenshots & Visuals
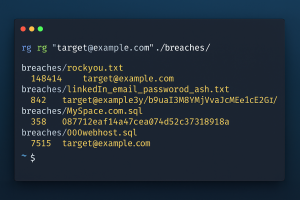
🕵️♂️ Step-by-Step Example Investigation
Scenario: A company suspects an attacker is using leaked employee credentials. You’re asked to investigate possible entry points.
- Search for Company Emails:
rg '@acmecorp.com' ./breaches/
Finds every appearance of company emails in the breach archives. - Audit Password Reuse:
Useholeheor a password script to see if the same passwords are used on social media or cloud accounts. - Correlate to Breach Sources:
Cross-reference results with the breach origin (Collection #1, LinkedIn, Dropbox) to assess risk. - Output Findings:
List exposed accounts, passwords, and recommendations for forced password resets.
⚖️ Legal/Ethical Disclaimer
Ethical Note:
Always use breach data with the highest respect for privacy, legality, and ethics. Only analyze data you are legally permitted to access, and never target individuals or organizations without explicit authorization.Unlawful use of breach data can lead to legal consequences and personal harm.
📊 Comparison Table: Local vs. Cloud Breach Checking
| Feature | Local Breach Archive | Cloud API (e.g., HIBP) |
|---|---|---|
| Speed | 🚀 Blazing Fast | ⏳ Variable |
| Privacy | 🛡️ 100% Local | 🕵️ Data sent externally |
| Rate Limits | ❌ None | ✅ Usually present |
| Data Depth | 📚 Full access | 📦 Limited to API scope |
| Cost | 💸 One-time (storage) | 💸 Ongoing/usage fees |
📚 Further Reading & Community Links
- r/OSINT Subreddit – Active OSINT community, tips, and news.
- OSINT Framework – Comprehensive collection of OSINT resources.
- DFIR Discord – Digital forensics and investigation chat.
- Breach Compilation (explained by Troy Hunt)
❓ FAQs
- Q: Is it legal to possess breach data?
- A: Laws vary by country. In most places, possessing publicly released breach data for research/education is not illegal, but distributing or using it for unauthorized access is.
- Q: How do I keep my breach archives secure?
- A: Use disk encryption, strong passwords, offline storage, and never upload breach data to cloud services without robust controls.
- Q: Are there risks in opening breach files?
- A: Yes. Files can contain malware, especially .exe, .scr, or macro-enabled documents. Only open text files and always scan with antivirus.
- Q: How often should I update my breach data?
- A: Update whenever major new breaches occur or when new compilations are released. Staying current increases the value of your local archive.
🗂️ Download & Resource Table
| Dataset | Download / Source | Approx. Size |
|---|---|---|
| HIBP Passwords | HIBP | 90 GB |
| RockYou2021 | GitHub | 8.4 GB |
| Collection #1-5 | Troy Hunt Blog | 220 GB (all) |
| Exploit.in | SecLists | 24 GB |
| Anti-Public | SecLists | 17 GB |
| OSINT/Mirror/Torrent sites | 33 GB+ | |
| Adobe | OSINT/Mirror/Torrent sites | 4 GB |
| MySpace | OSINT/Mirror/Torrent sites | 22 GB |
| Dropbox | OSINT/Mirror/Torrent sites | 5 GB |
| Facebook/Twitter | OSINT/Mirror/Torrent sites | Varies |
📨 Ready to go deeper?
Ready to go deeper?
Subscribe to our newsletter for more practical OSINT, data breach deep-dives, and exclusive tool tutorials.
Join the conversation: Have a favorite breach tool or dataset? Share your experience in the comments below, or suggest what you want us to explore next!
🚀 Level Up Your OSINT with Local Breaches
Having local breach data isn’t just for elite hackers—it’s now a baseline capability for anyone serious about open-source investigations, security audits, or adversarial research. With the right starter pack and local tools, you’ll be faster, more private, and able to uncover insights the cloud tools can’t touch.
Want the full “OSINT Arsenal” blog series?
Stay tuned—the next post will cover the ultimate toolkit for researchers in 2025 and beyond.

You must be logged in to post a comment.